Introduction
OpenID Connect is pretty much a standard of Single Sign On authentication. You probably logged into many applications using your Facebook or Google account. Here, i.e, Facebook is serving as an identity provider that confirms, that this is really you who logged in. Some other application can use this knowledge (if you let them), to identify you, and effectively, log you in.
OpenID connect standard is not easy to understand, it consists of many different authentication flows, for many purposes, like websites, mobile apps, and other. This document would not cover this topic, as it's very broad. For more information, refer to some official documentation, or some easier to understand tutorial 1, or tutorial 2. Without any knowledge of OIDC standard, the rest of the document may seem hard to understand, so some reading first is highly recommended.
Before you start
Make sure you have proper system permissions:
- Go to the PGM -> Clubs -> Employees -> System permissions.
- Click on the "Permissions" button.
- Check if the API is marked, as well as CreateApiClients and OpenIdMemberLogin permissions:
- CreateApiClients - allows you to create an API client - without this, no integration would work. Taking back this permission makes all already created clients unusable. It's required for other permissions to even work.
- OpenIdMemberLogin - this permission allows to integrate third-party applications with ClientPortal and in future also with API using OpenID Connect standard. More on this topic in
- If you don't know how to set these permissions, check this article.
Instruction
API clients
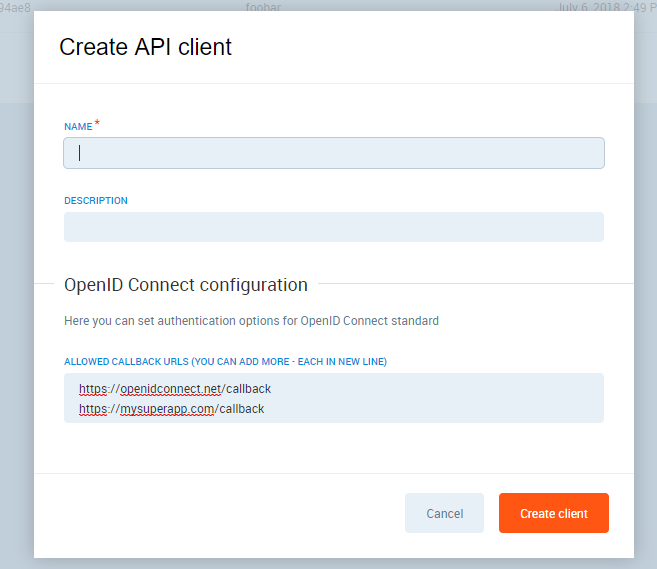
To start integrating with OIDC you need to create an API client. More information on what does it mean, and how to create an API client is in this article. The only difference is that you also need to define allowed callbacks. Callbacks are detailed in OIDC tutorials, so please refer to them.
OpenID Connect endpoints
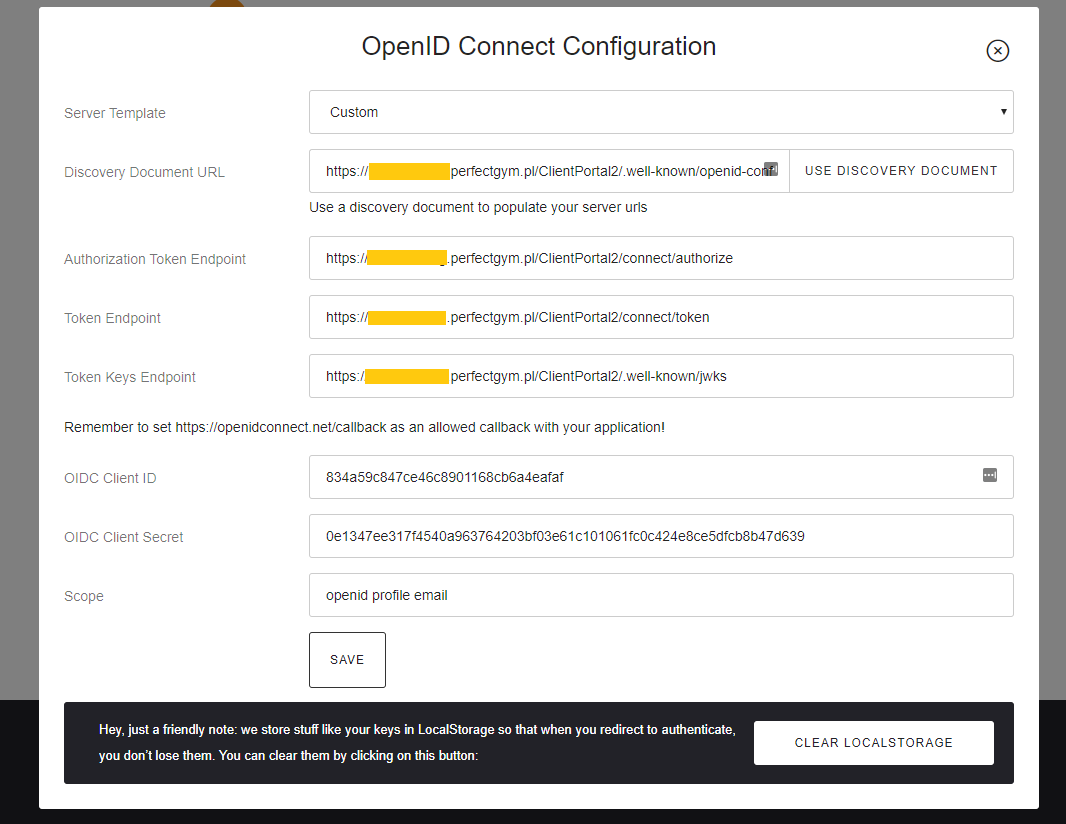
OpenID Connect provider is embedded into ClientPortal2 application. You can find it by querying the OIDC discovery document: https://companyname.perfectgym.pl/ClientPortal2/openid/.well-known/openid-configuration.
Here, you will find any auth endpoints you need to make an OpenID authentication flow, along with auth scopes.
OpenID Connect authentication flows
For now, we are only supporting authorization code flow. Implicit and hybrid flows are to be implemented.
Testing the integration
You can use the online tool to test your setup. Remember to include its callback URL into allowed URLs (info above). The easiest way is to load configuration via discovery document:
Tokens, that you would retrieve via authentication consist of identity token and access token. Identity token is a JWT (JSON web token), which you can decode into member data. It is required to include openid scope in auth request to retrieve it.
You can easily decode contents of identity token for testing purposes via https://jwt.io/. Currently, access token is not being used by any of our applications. It's only included to be OIDC compliant. In the future, it will allow integrating with our API also.